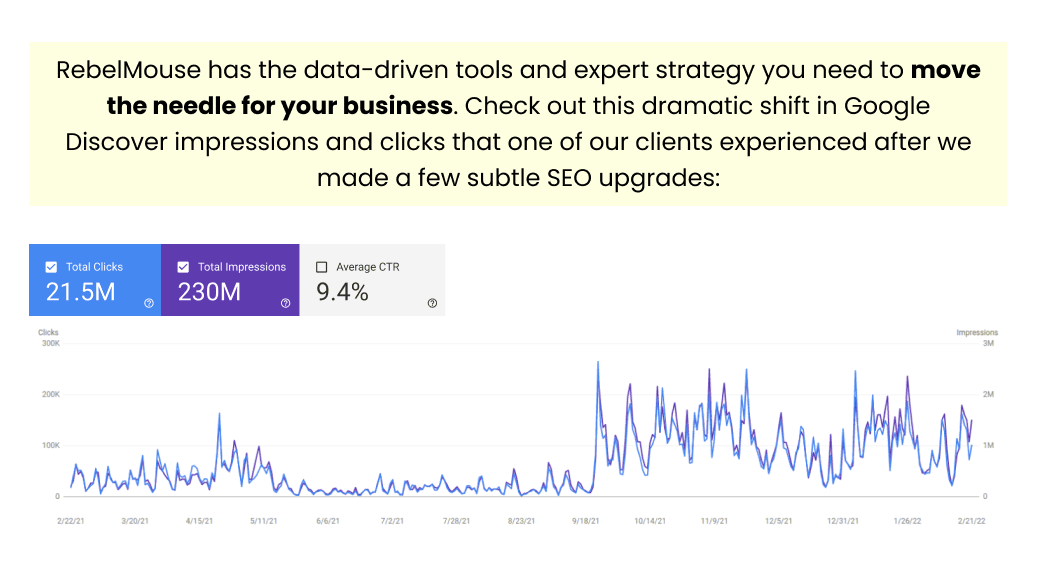
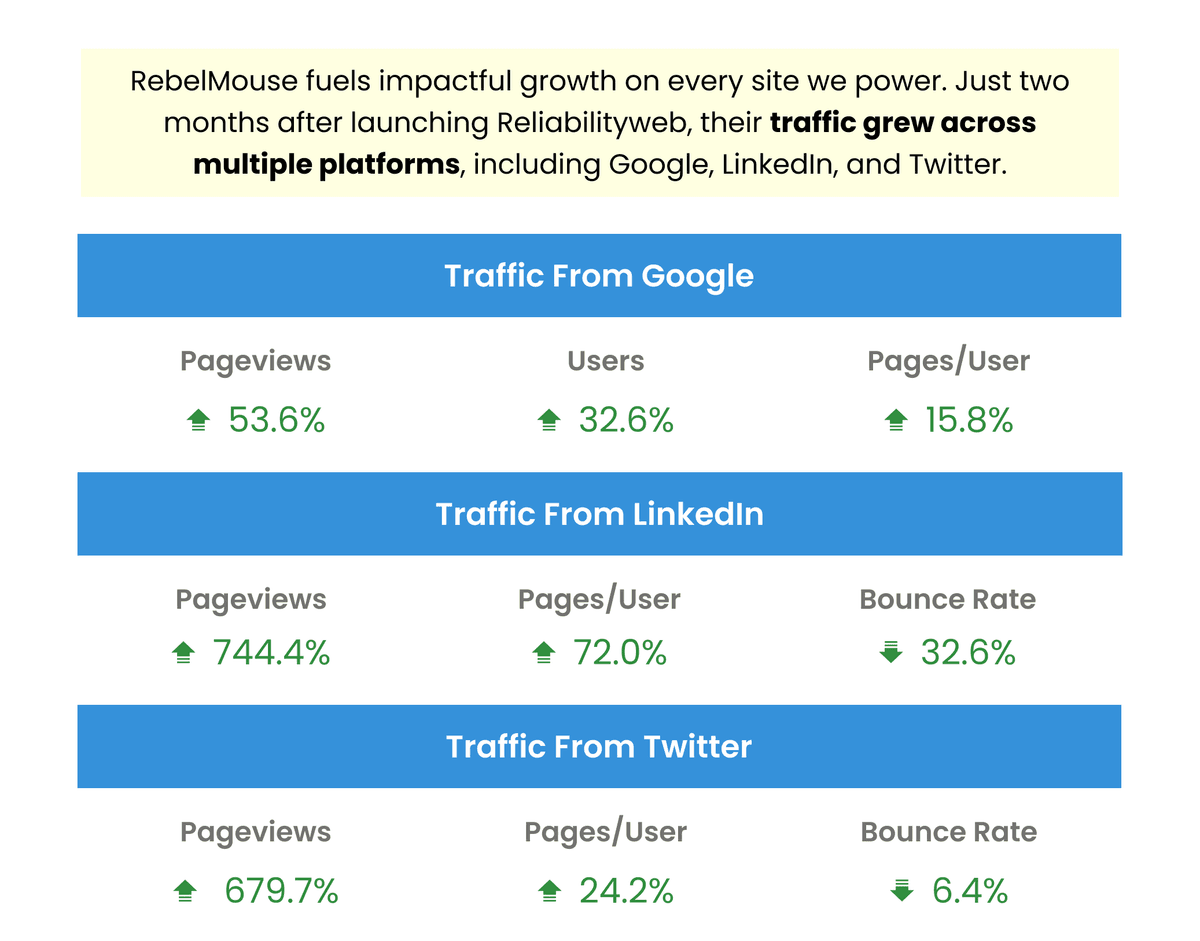
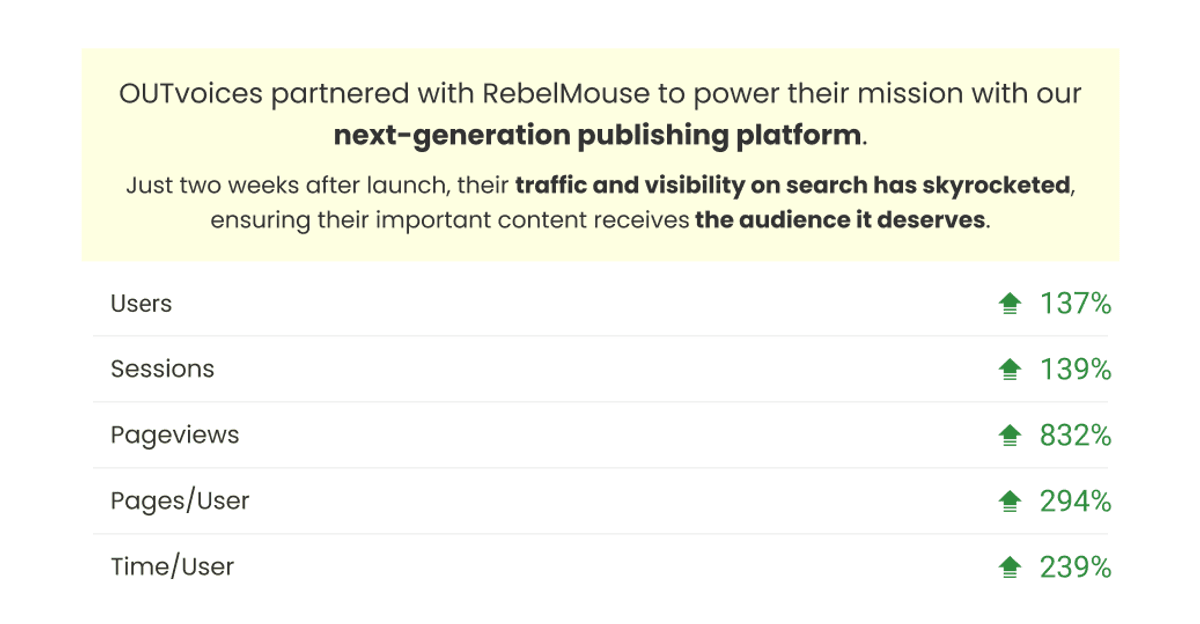
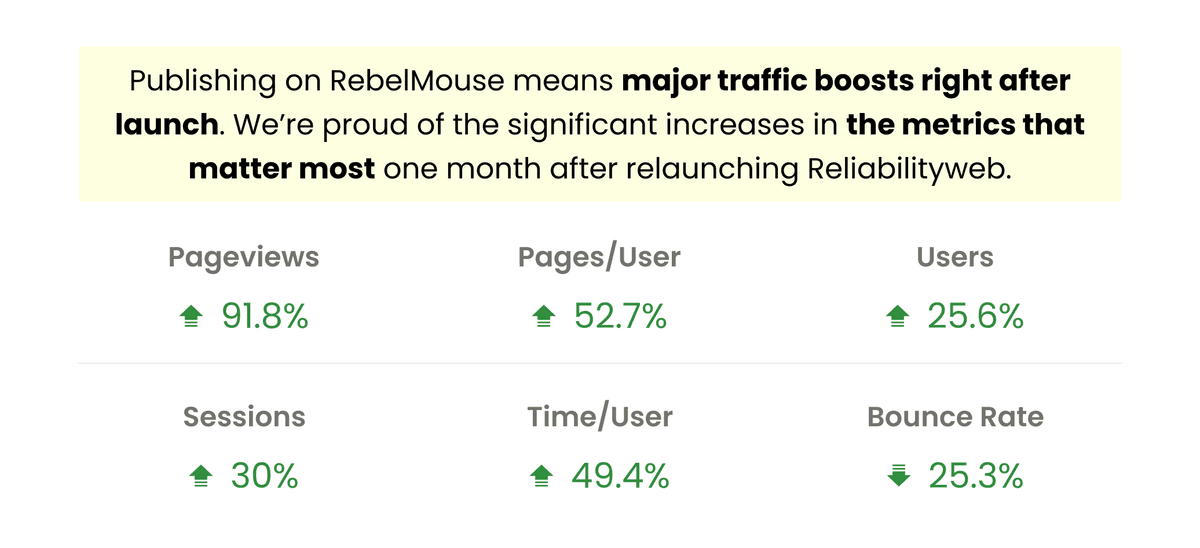
To ensure every site powered by RebelMouse is high performing, secure, and optimized for user experience, we only use the best and most reliable methods to host our infrastructure. Here's a detailed look at some of the services and security measures we use every day to secure maximum stability and security for each of our sites.
Click here to learn more about what makes RebelMouse secure, stable, redundant, and high performing.
Services
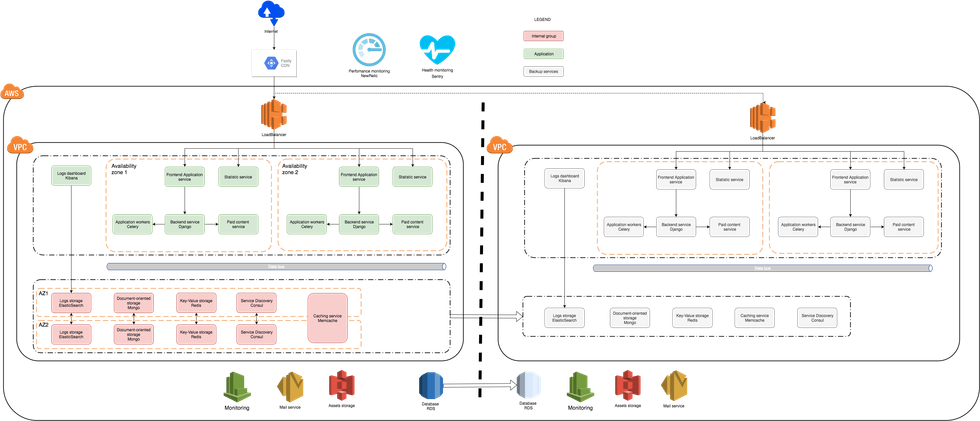
Stateless services, such as application services for front end and back end tasks, are deployed within an Amazon Virtual Private Cloud (VPC) into multiple availability zones using Amazon Auto Scaling groups. Every service deployment is automated and can be done without an operator. Auto Scaling groups eliminate the need for manual recovery procedures in the event of hardware-related incidents. Additionally, Auto Scaling groups for stateless services provide the ability to balance resources according to current load.
Stateless services include:
- Front end and back end applications
- Background workers
- Dedicated services for paid content and statistics
All interactions with our internal services are done via Amazon Elastic Load Balancing (ELB). Load balancing allow us to control the flow of all incoming traffic and reroute it to the group of instances that are available as necessary, which covers any networking and hardware issues. Every load balancer controls the health of the listener instance by regularly performing health checks and removing failed instances from production environments.
Load balancing and Elastic Compute Cloud (EC2) instances provide monitoring services with resource consumption data. Stateful services such as MongoDB, Redis, and Memcached are deployed within a VPC into multiple availability zones using Auto Scaling groups. Every data service has backup, recovery, and automatic failover procedures. Backup and recovery procedures are integrated into Auto Scaling groups and tested regularly.
Services performance is monitored by internal and external tools:
- Sentry is used to track errors.
- New Relic is used for application performance monitoring.
- Amazon CloudWatch is used to monitor performance extremes.
- Monit, Nagios, and Cacti are used to monitor metrics per instance.
Security
Defense in Depth (DiD) standards are adhered to and applied at all levels:
- Amazon Web Services (AWS), such as Identity and Access Management (IAM) and CloudTrail
- VPC and subnets
- Load balancers (security groups)
- EC2 instances
- Operating systems use permissions-based controls
Access Monitoring:
- AWS CloudTrail monitors all activities in our production data centers and grants us the ability to perform audits
Data Protection:
- Secured storage
- Encrypted transition protocols
If you have any questions about RebelMouse's technical infrastructure, email support@rebelmouse.com .